Credssp Encryption Oracle Remediation
May 10, 2018 CredSSP Encryption Oracle Remediation Policy Settings There are three settings contained in the policy setting that can be enabled. Force Updated Clients: Client applications which use CredSSP will not be able to fall back to the insecure versions and services using CredSSP will not accept unpatched clients. How to fix remote desktop error CredSSP Encryption Oracle Remediation. This caused by Windows was updated the patches that causes some server could not remote desktop. Change the group policy Encryption Oracle Remediation default setting from Vulnerable to Mitigated. This RDP authentication issue can occur if the local client and the remote host have differing Encryption Oracle Remediation settings that define how to build an RDP session with CredSSP. If the server or client have different expectations on the.
OverviewWith the release of the March 2018 Security bulletin, there was a fix that addressed a CredSSP, “Remote Code Execution” vulnerability (CVE-2018-0886) which could impact RDP connections.
Remote Desktop connectionAn authentication error has occurred.The function is not supported.Remote Computer: hostnameThis could be due to CredSSP encryption oracle remediation.This error is caused by the fact that on Windows Server or desktop Windows versions, to which you are trying to connect using RDP, since March 2018 there were no security updates installed. In March 2018, Microsoft released an updates that blocks remote code execution using a vulnerability in the CredSSP protocol (bulletin CVE-2018-0886). After successfully connecting to a remote RDP server (computer), you need to install the missing security updates on it through the Windows Update (verify that the service is enabled) or manually. Below are direct links to updates for Windows Server, which must be installed:. Windows Server 2012 R2 / Windows 8 –.
Windows Server 2008 R2 / Windows 7-. Windows Server 2016 / Windows 10 1607 –After installing the updates and rebooting the server, don’t forget to disable the policy on the clients (either switch it to the Force Updated Clients), or return the value of the AllowEncryptionOracle registry parameter to 0. In this case, your computer will not be at risk of connecting to unprotected hosts with CredSSP and exploitation of the vulnerability.REG ADD HKLMSOFTWAREMicrosoftWindowsCurrentVersionPoliciesSystemCredSSPParameters /v AllowEncryptionOracle /t REGDWORD /d 0. RADJ,Sorry I’ve just seen your replyQ: Have you disabled NLA on the server side? A: YesQ: Do you use Windows Server 2003 / Win XP or something similar as an RDP server?
Credssp Encryption Oracle Remediation Regedit
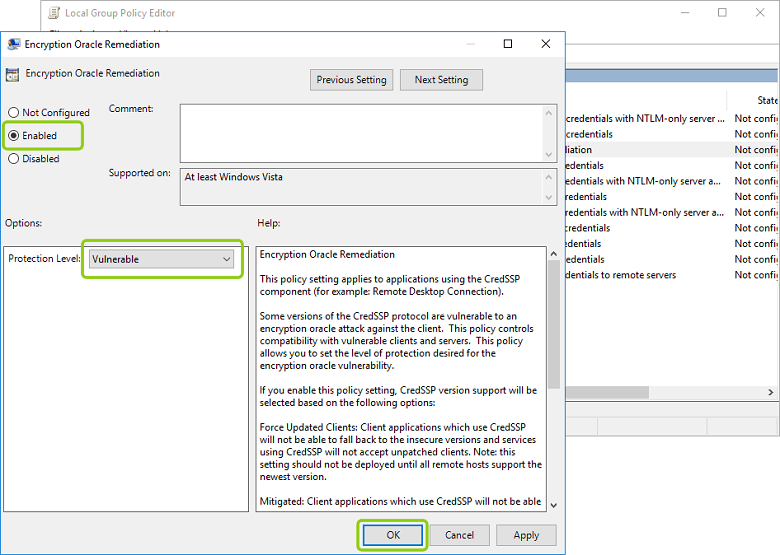
A: NoQ: What is the Windows version on the client? A: Windows 7Q: Did you enable the policy Oracle Remediation Encryption = Vulnerable on the client computer? A: NoAs the server can’t be updated, it doesn’t has that group policy to configureSo the quick fix was to deselect that box.In this other site I saw a regedit solution:Reply. Most likely the AllowEncryptionOracle = 2 registry parameter on computers with Windows XP will not work. Most likely, to connect to RDS from clients on XP, you need to switch the Encryption Oracle Remediation policy to the Mitigated/ Vulnerable level on terminal servers. However, the RDS server will be vulnerable to the exploitation of the CredSSP vulnerability (CVE-2018-0886).
Credssp Encryption Oracle Remediation Server 2012
You will also have to disable the Network Level Authentication on RDS server (however, there is also a workaround for enabling NLA in Windows XP SP3). Those, it should be used only as a temporary solution, until you update the OS on clients to Windows 10 / 8.1 / 7.